All Courses
Author:
- All
- Abdul Rahman
- Aleksey Grebeshkov
- Ales
- Alexander Polyakov
- Alton Hardin
- Amerigio Picio
- Amit Huddar
- Andrew Schlegel
- Arsalan Saleem
- AZHAR MD NAYAN
- Babar Hussain
- Carlos Solís Salazar
- CIP Cyber
- Colin MacGregor
- Corey Charles
- Corey Charles
- Corey Charles
- Corey Charles
- Derek Armstrong
- Development Island
- DreamVision IT LLC
- DreamVision IT LLC / STC Computer Forensic Group
- EH Academy
- ehacking
- Emin Caliskan
- Enix Hamoji
- Fadi Derbas
- Frank Hissen
- Frank Hissen
- Gabriel Avramescu
- Gautam Kumawat
- Georgia Weidman
- Geri Revay
- Hailey Huynh - Customer Success Executive, CIP Cyber
- Hailey Huynh - Customer Success Executive, CIP Cyber
- Hussam Khrais
- Infosec4TC
- InSEC-Techs
- Irfan Shakeel
- Irfan test
- Issam Baou
- Jane Smith
- Jason cohen
- Jean Claude Mudilu Kafunda
- John Ntambi
- Joydip ghosh
- Juravlea Nicolae
- Lazaro (Laz) Diaz
- LearnSmart
- Luciano Ferrari
- MBPSec Tech
- MBPSec Tech
- Mike West
- Mohamed Atef
- Mohamed Ramadan
- Mr technical
- Mudar Abbas
- Muhammad Ali
- Nop Sled
- Nop Sled
- Nop Sled
- OneLit
- Parwiz
- Patris Koushesh
- Peter Dalmaris
- PHMC SECURITIES
- Priyank Gada
- RANJAN RAJA
- Saad Sarraj
- sachackken
- Security Skills Hub
- Shaun Kolich
- Shon Gerber
- Stone River eLearning
- Sunil Gupta
- Teach Me School
- TechMe
- test author
- Timur Mezentsev
- Ts. Azhar Bin Md Nayan
- Visadi Khalikov
- Vishal Patel
- Wayne Walker
- Zaid Sabih
Cybersecurity Fundamentals for Aspiring Security Professionals
Building Strong Cybersecurity Skills from Scratch: A Comprehensive Course for Novices in the Field
Irfan Shakeel
Ethical Hacking Practices for IT and OT
Securing IT and OT Infrastructures: A Comprehensive Guide to Ethical Hacking
Irfan Shakeel
Secure Configuration of Siemens S7-1200 PLC
Learn best practices to secure and configure Siemens S7-1200 PLC for safe and reliable industrial automation operations.
CIP Cyber
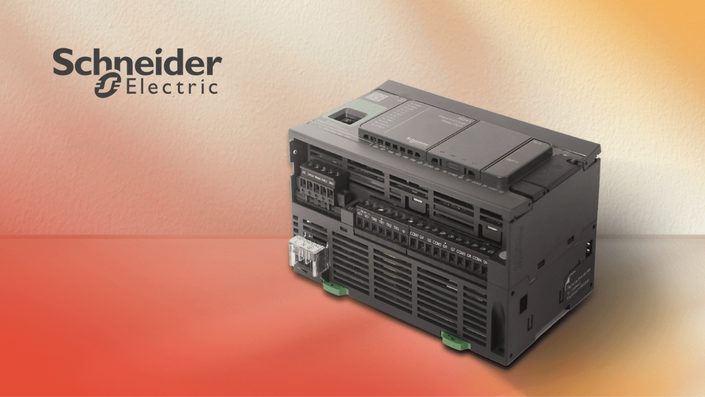
Configuring Schneider TM241CEC24R PLC for Maximum Security
Enhancing Industrial Cybersecurity Skills: A Comprehensive Training Program for Configuring Schneider TM241CEC24R PLC with Maximum Security
CIP Cyber
Certified OT Security Professional (COSP)
Securing Industrial Control Systems: A Comprehensive Introduction to ICS Cyber Security
CIP Cyber
Rockwell MicroLogix 1100 PLC Security and Configuration
Building resilience against cyber threats: Rockwell MicroLogix 1100 PLC secure configuration training
CIP Cyber
Mastering Kali Linux: A Comprehensive Guide to Linux Fundamentals
Learn the Basics of Kali Linux and Advance Your Skills in File Systems, Command-Line Interface, and Shell Scripting
Irfan Shakeel
Malware Analysis & Reverse Engineering for Beginners
Unveiling the Secrets of Malware: A Beginner's Guide to Malware Analysis and Reverse Engineering
CIP Cyber
The Complete OSINT Training Program
Launched in 2021, the Most Effective OSINT Training Program
Irfan Shakeel
JOURNEY TO THE ANONYMITY ON THE INTERNET
TOR: WHAT, HOW, WHEN AND WHY? How to Become Anonymous in 2017?
Irfan Shakeel
VoIP Hacking & Penetration Testing Training
Learn the art of VoIP Penetration Testing
CIP Cyber
Ethical Hacking & Penetration Testing using Kali Linux
Exploit the vulnerabilities with Nmap, Metasploit and other tools
CIP Cyber
Python Hacking for Cybersecurity Professionals
When other's tools fail, writing your own makes you a true pentester!
CIP Cyber
The Complete Ethical Hacking Certification Course
Master Ethical Hacking, Kali Linux, Cyber Security, System Hacking, Penetration Testing
CIP Cyber
Mobile Penetration Testing - iOS, Android & Windows
PenTesting iOS and Android Applications
CIP Cyber
Metasploit training for Penetration testing & Ethical Hacking
Cyber Security Training using Metasploit
CIP Cyber
© 2023 CIP Cyber. All rights reserved.